| 进程控制流完整性保护技术综述 |
| |
| 作者姓名: | 张正 薛静锋 张静慈 陈田 谭毓安 李元章 张全新 |
| |
| 作者单位: | 北京理工大学计算机学院,北京 100081;北京理工大学软件学院,北京 100081 |
| |
| 基金项目: | 国家自然科学基金(U1936218, 62072037); 之江实验室开放课题(2020LE0AB02) |
| |
| 摘 要: | 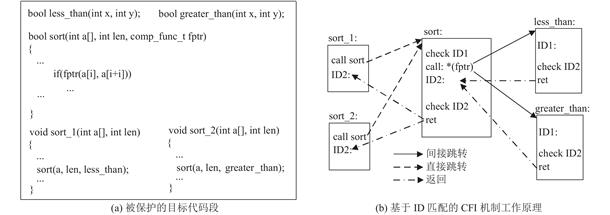
控制流劫持攻击利用程序内存漏洞获取程序的控制权,进而控制程序执行恶意代码,对系统安全造成极大的威胁.为了应对控制流劫持攻击,研究人员提出了一系列的防御手段.控制流完整性是一种运行时防御方法,通过阻止进程控制流的非法转移,来确保控制流始终处于程序要求的范围之内.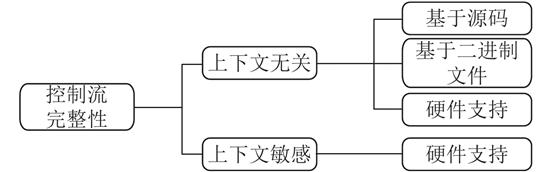
近年来,越来越多的研究致力于解决控制流完整性的相关问题,例如提出新的控制流完整性方案、新的控制流完整性方案评估方法等.首先阐述了控制流完整性的基本原理,然后对现有控制流完整性方案进行了分类,并分别进行了分析,同时介绍了现有针对控制流完整性方案的评估方法与评价指标.最后,对控制流完整性的未来工作进行了展望,以期对未来的控制流完整性研究提供参考.

|
| 关 键 词: | 控制流完整性 控制流劫持 控制流图 系统安全 |
| 收稿时间: | 2021-05-02 |
| 修稿时间: | 2021-06-24 |
| 本文献已被 万方数据 等数据库收录! |
| 点击此处可从《软件学报》浏览原始摘要信息 |
|
点击此处可从《软件学报》下载免费的PDF全文 |
|




